It is now 14 years since the European Commission designated 28 January as the European Data Protection Day, with the aim of promoting, raising awareness and reporting on the rights and obligations that users have over their personal data on the internet.
This day was chosen because it coincided with the signature of The Council of Europe Convention 108 (Data Protection Convention), where the protection of individuals with regard to the automated processing of personal data was approved. It is celebrated globally and is known as the “Data Protection Day”.
From the security group of inLab FIB (esCERT) we want to contribute our grain of sand offering a series of tips (good practices), information on activities scheduled for this day, and recommended readings.
Best practices:
So that there is no doubt about what is considered personal data, we leave the definition given to us by the General Data Protection Regulation (GDPR) of the European Parliament:
Personal data: any information about an identified or identifiable natural person (the data subject); any person whose identity may be determined, directly or indirectly, in particular by an identifier, such as a name, an identification number, location data, an online identifier or one or more elements of the physical, physiological, genetic, psychic, economic or social identity of that person, shall be considered an identifiable natural person. Person. The new regulation also covers other types of identifiers such as online identifiers provided by personal devices, applications, tools and protocols, such as internet protocol addresses, session identifiers in the form of “cookies” or other identifiers, such as radio frequency identification tags.
1) Who do I give my data to?
Any application or website that intends to collect any data that can be identified as personal, either with forms (Name, surname, ID…) or in a transparent way (location, IP, cookies…) must explain the reasons why you need that data, that use will give you and explicitly ask for permission to collect and use it. Therefore, we recommend:
- Be wary of applications or websites where you are asked for data and there is no explicit request for consent.
- Check the apps you have given permission to a certain frequency, in case the terms and conditions of use of your data have changed. They have an obligation to notify you in case they make changes, but sometimes we ignore those messages. It is important to take them into account and above all, if you have not received a message of change of conditions, if these have occurred, you can report them to the corresponding data protection agency (APDCAT or AEPD).
- In the information they offer about the use, they must also indicate how to unsubscribe in case at any time you want to do so.
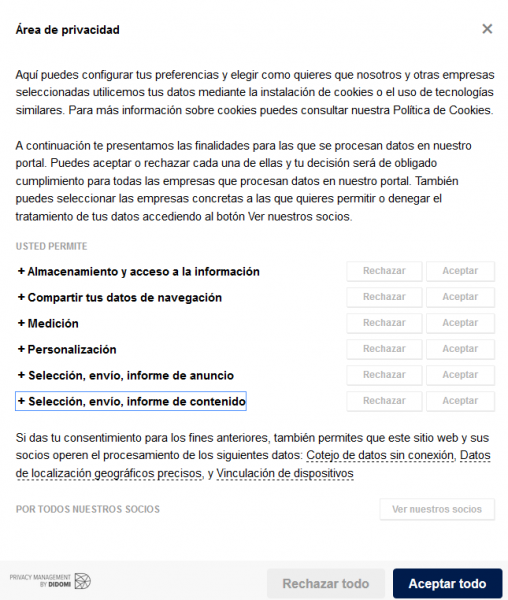
Because these measures are mandatory since the GDPR came into force, you will see that most applications and websites inform you and request your consent, it is important that you read it and do not give quickly to OK (I accept the conditions):

If instead of giving the OK, you click “More Information”, you will be able to choose whether or not to give them access to the data they ask for, something like this will usually come out:
2)How to prevent the theft of my data?
Data theft can occur in many ways but the most frequent is the one we know as “Phishing”, tricking the user into getting their credentials and other data, with the consequent danger of misuse of them. According to APWG’s latestPhishing Activity Trends Report, 3rd Quarter 2019,the number of phishing attacks increased in the third quarter of 2019, to a level not reached since the end of 2016. The most common ways to perform these thefts are:
- Injecting a malicious program (malware) into the victim’s computer or mobile device that captures the key-logger to identify usernames and passwords, and send them to the control center that collects them.
- Sending the victim to a fake web page (looking like the web whose access is to be stolen) in which they are asked for login credentials (identifier and password) and in some cases other personal data.
- It’s also done more selectively through phone calls or emails, for example, calling as microsoft support or someone in your bank office.
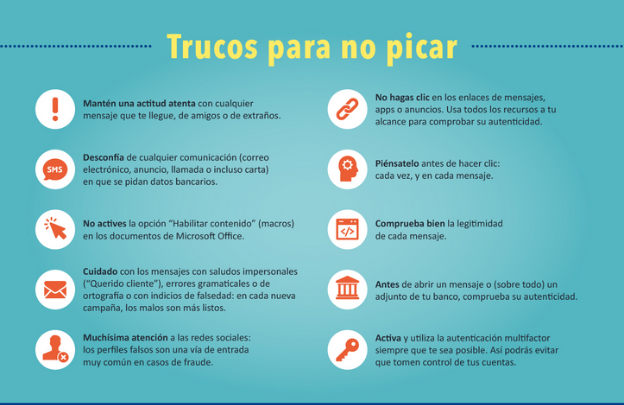
The tips to be followed to avoid such attacks are very well reflected in the infographic offered by APWG:
3) How to protect my data?
Two are the key points in terms of data protection that we should all always keep in mind:
- How is my data protected?: Where and how do we store our access data (users, passwords, certificates..) to the different services and applications that we can access by identifying ourselves with them. Do we tell the application to remember them, do we write them down on a piece of paper or in a text file? To properly protect our access data, simply follow 4 basic rules:
- Passwords must be secure, at least 10 characters, not to use personal data for the password, it can be as long as you want, the longer it is less likely that they can get it right.
- Never use the same passwords for different services or applications.
- Always try to use second factor authentication for those services or applications that implement it.
- Use a password manager to save passwords, these managers store all account-related information (login, application name, password…). The advantage of using them is that you only have to memorize a password, that of the manager. Some managers that we recommend:
- If I lose them, can I recover them?: Good password managers only allow you to recover them through backups of personal data access to applications. Therefore, we must do them frequently. These copies must be on external devices or in cloud storage and must be protected (encrypted or password-enabled) to prevent illegitimate access to them in the event of theft.
Conferences and activities scheduled to celebrate this day:
- From the NCSA (National Cyber Security Alliance) there will be an online and free Access event, no registration is required:
- The data protection agency of Catalonia:

