In terms of security and networks, the concept of spoofing refers to the set of techniques through which an attacker impersonates a legitimate entity by falsifying data in a communication.
There are several types of spoofing, but the most important are the following:
IP spoofing
Before going into what this type of spoofing consists of, it is necessary to know what an IP packet is. In networking, a packet is a small segment of a larger message. Data sent over a network is divided into packets, and these are combined by the final recipient to reconstruct the complete message. Thus, an IP packet is an IP (Internet Protocol) packet.
These types of packets have two very distinct parts: the IP header and the data. In the following image, we can see the format of the IP header and its fields.
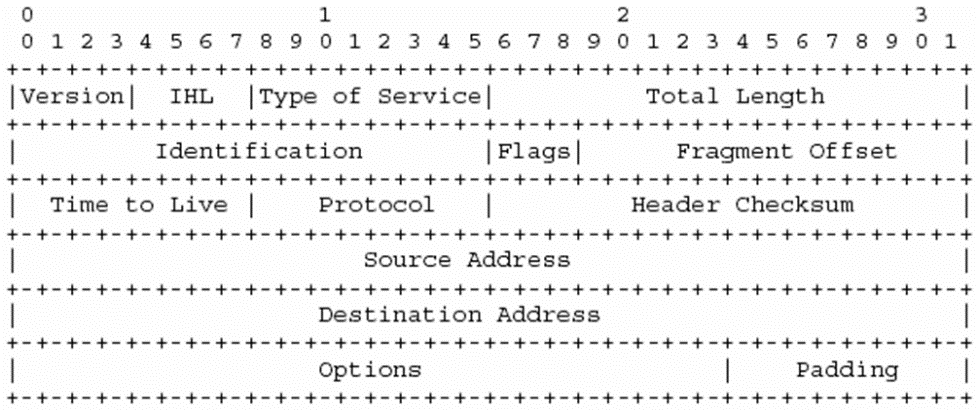
The two most important fields are the source and destination address, which specify who has sent the packet and therefore to which address it should be replied (if applicable) and the final recipient of that packet.
IP spoofing, essentially consists of substituting the source IP address of an IP packet. In this way, the attacker can send frames impersonating someone else. For this reason, any protocol encapsulated over IP is susceptible to this type of spoofing.
Carrying out this type of attack is very easy and quick to perform, since, as we have seen, it is simply a matter of modifying a field in the header. However, it should be noted that the recipient will respond to the supposed sender address of the packets (the spoofed address) and not to the attacker. For this reason, this type of spoofing, together with broadcast requests, is used to commit flooding attacks, without the need to obtain any response.
ARP spoofing
ARP (Address Resolution Protocol) is a protocol responsible for finding a physical address (Ethernet MAC) that corresponds to the IP address to which the user wants to send data. For this reason, each device has an ARP table with IP-MAC associations.
In other words, we assume that Bob has a letter for Alice, but doesn’t know which mailbox to drop it in. That is, Bob knows to whom he has to send the letter (@IP), but not in which physical mailbox to drop it (@MAC). In this case, Bob will consult his ARP table and find the entry:

Now Bob knows which mailbox (@MAC) to deliver the letter to.
ARP table spoofing involves the construction of modified ARP request and response frames to alter the ARP table (i.e., the IP-MAC relationship) of a victim and force it to send IP packets to the attacker.
Going back to the previous analogy, an attacker can make Bob believe that he is leaving the letters in Alice’s mailbox, when he is really leaving them in the attacker’s mailbox.
DNS spoofing
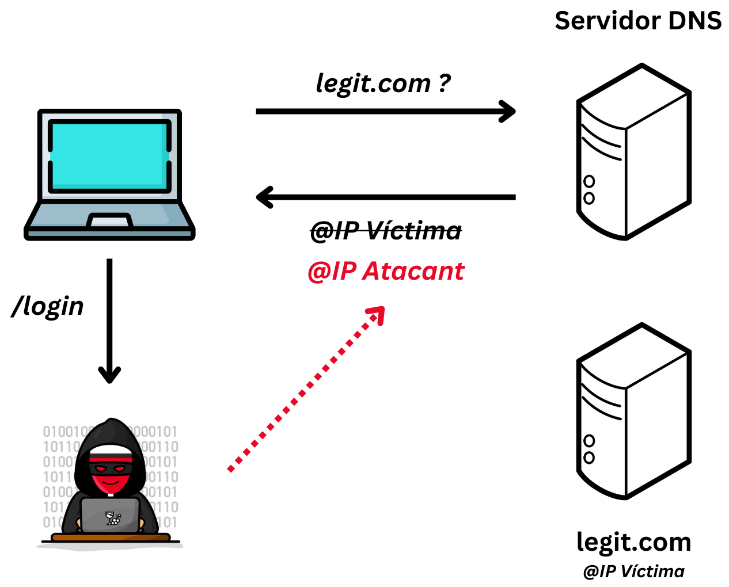
This type of spoofing consists of falsifying the relationship between the domain name and an IP in the DNS name resolution query. This is achieved by manipulating the entries of a DNS server. For example, let’s assume the following case:
The legit.com domain resolves to the @IP-Victim address.
An attacker manages to spoof DNS server entries in such a way that it responds to resolutions from this domain to another IP (e.g. @IP-Attacker).
Now, requests to legit.com will be resolved to @IP-Attacker.
It is worth mentioning that carrying out this type of spoofing as well as the previous one is only possible if the attacker is within the same network as the victim devices. The effectiveness of this type of attack is greatly reduced when we are in secure networks and use HTTPS connections (encrypted communication). Hence the importance of connecting to secure networks.
E-mail spoofing
Email spoofing is the creation of email messages with a false sender address. This type of spoofing is easy to perform since the basic email service protocols do not have any authentication method. This is due to the fact that at the time of its creation, security was not an issue or a relevant aspect.
Spam and phishing emails use this type of spoofing to deceive the victim about the legitimacy of the sender. The recommended measures to prevent these attacks are to create SPF DNS records and DKIM digital signatures.
It is important not to confuse the term spoofing with phishing. Phishing refers to a set of techniques aimed at deceiving the victim, gaining their trust in order to manipulate them or make them perform involuntary actions.
Phishing is the WHAT and spoofing is part of the HOW.
Conclusions
To conclude, there is currently a general unawareness and lack of knowledge on the part of organizations about spoofing and its countermeasures. In addition, it is not uncommon to find, despite using the preventions, a misconfiguration of these, which results, in many cases, to remain vulnerable to phishing attacks.
It should be emphasized that, as is often said, the most vulnerable asset is people. Good awareness and training for these types of attacks, which take advantage of people’s trust and lack of knowledge, are the key to stopping these threats.
