Open Source, SIEM and XDR
First, we will have to explain these concepts introduced in the title to understand the Wazuh framework; SIEM and XDR.
SIEM (Security Information and Event Management) is a technology that collects, analyzes and correlates data from different sources in real time to identify and respond to security threats. Sources can be logs from systems, applications, network or end devices. It uses correlation and analysis techniques to identify patterns of malicious behavior and generate alerts when suspicious activity is detected. It also incorporates report generation functions, as well as graphical forms of visual representation.
XDR (Extended Detection and Response) goes further by extending its reach to a wider range of devices and/or services (sources).
In addition, it not only has a passive detection role, but also has the capability of automated active response, which allows action to be taken in the event that malicious behavior is detected.
Wazuh therefore incorporates a whole range of features and functionalities that allow it to work as a SIEM and XDR. But first we will explore its architecture.
Wazuh’s architecture
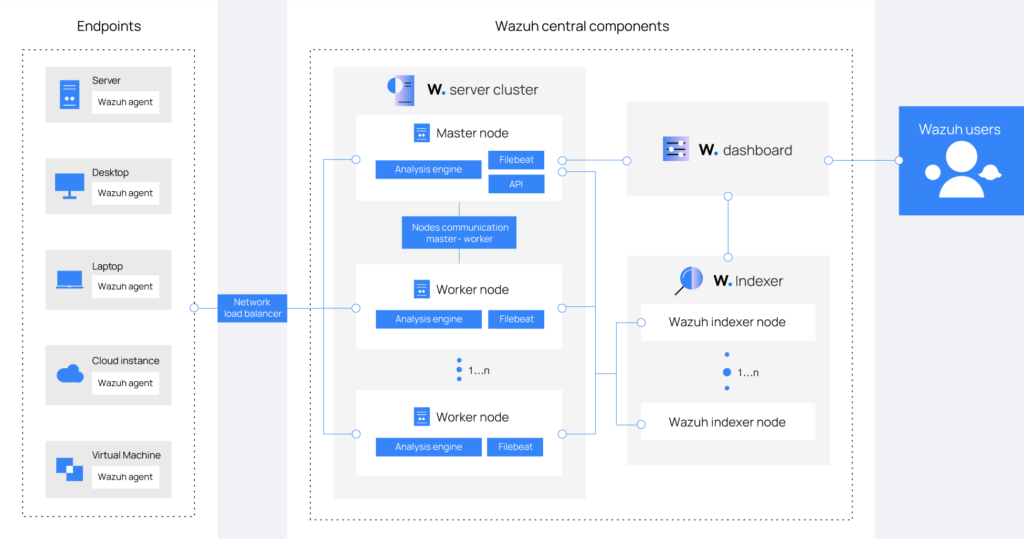
The solution is based on deploying an agent on the monitored end devices (endpoints) and three core components: the indexer, the server, and the dashboard, which can be installed on one or several nodes, forming a cluster, thus improving performance, security and availability.
These are all the necessary components for the operation of Wazuh.
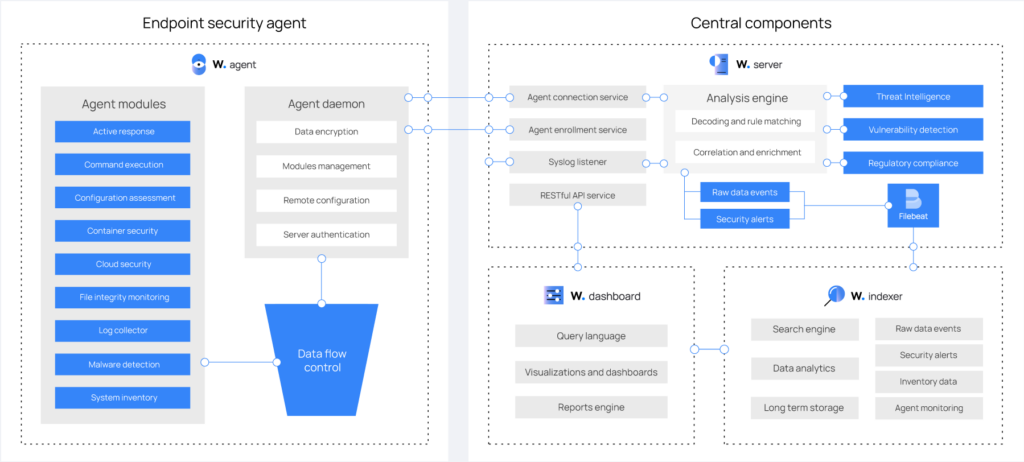
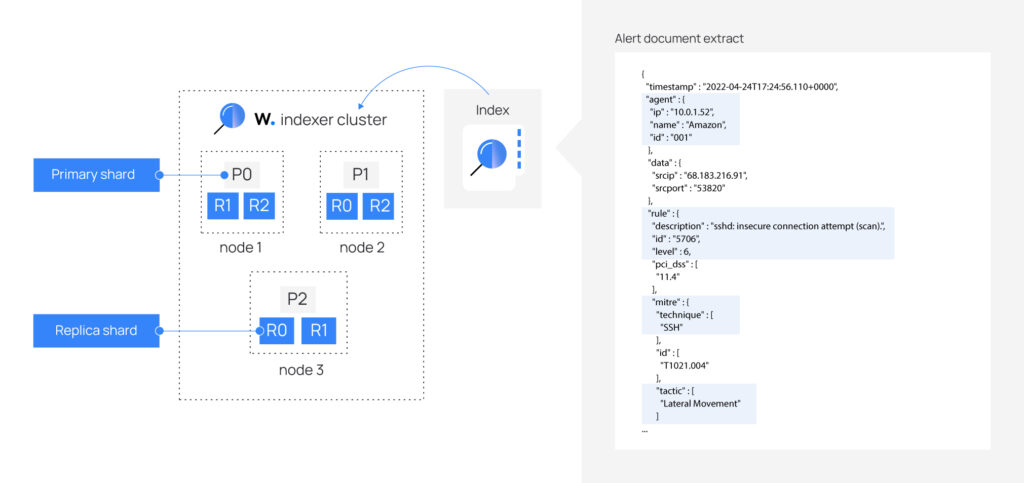
The indexer is highly scalable and has a full-text search and parsing engine. Indexes and stores the alerts generated by the server in documents in JSON format. These documents are distributed in different containers called shards, and by distributing these shards in different nodes we can ensure redundancy, improve the tolerance to hardware errors as well as increase the query capacity when we attach the nodes in a cluster.
In addition to speed, scalability and resilience, Wazuh’s indexer also includes features such as data roll-ups, alerting, anomaly detection and index lifecycle management.
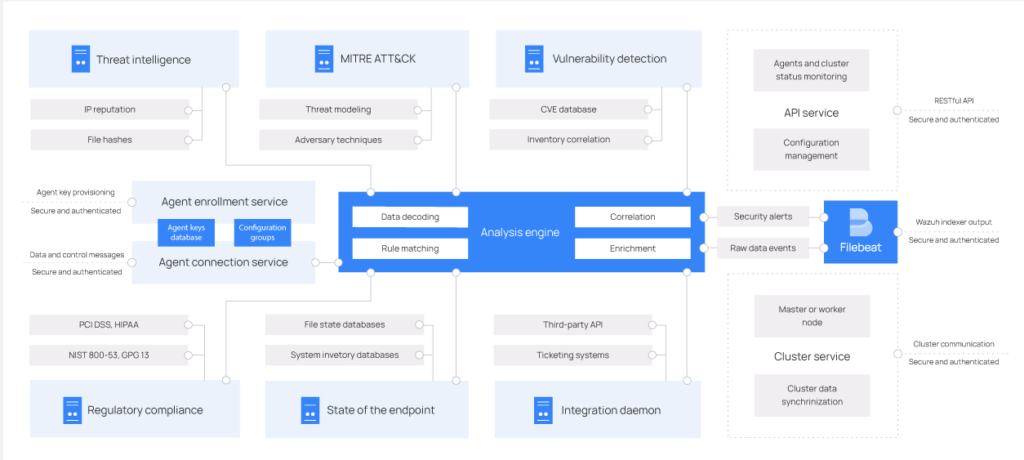
The server analyzes the data received from the agents and processes them through decoders and rules, using threat intelligence to detect known indicators of compromise (IOCs). A single server can analyze data from hundreds and thousands of agents and can scale horizontally in the form of a cluster. Additionally, through the server, it is possible to manage the agents remotely. The alerts use the MITRE ATT&CK framework and compliance requirements such as GDPR.
The server runs the following services: the analysis engine, the RESTful API, the agent registration service, the cluster daemon and Filebeat, which is used to send information to the indexer.
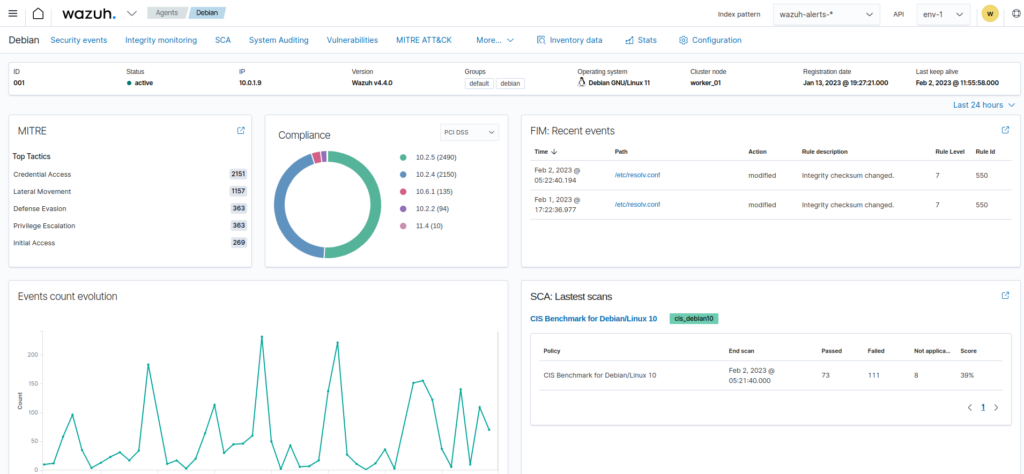
El dashboardés la interfície web perquè l’usuari pugui visualitzar les dades recollides i l’anàlisi dels esdeveniments i alertes de seguretat generades. It incorporates several functionalities that we will see later.
The agents are installed on end devices, such as desktop computers, servers, cloud instances or virtual machines. They allow the prevention, detection and response to threats, with the ability to operate in different operating systems.
An interesting point of Wazuh is that the mentioned end devices are agent-based (requiring the installation of software), but it also allows monitoring agent-less devices (without agents) such as firewalls, switches, routers or NIDS (Network Intrusion Detection System).
Therefore, the global structure of Wazuh and its components is as follows:
Functionalities and use cases of Wazuh
- SCA (Security Configuration Assessment):
Wazuh monitors system and application configuration to ensure compliance with security standards and policies. Wazuh agents perform periodic scans to detect misconfigurations or security holes in end devices that could be exploited by malicious actors. These configuration checks can be configured to adapt them to the needs of the organization. - Malware detection:
Wazuh detects malicious activity and generates indicators of compromise that occur on end devices as a result of malware infections or cyberattacks. - FIM (File Integrity Monitoring):
Wazuh monitors the folder system, identifying changes in the content, permissions, ownership and attributes of the files to be monitored. - Threat detection:
Wazuh offers comprehensive visibility to end devices and monitored infrastructure. It has record retention, indexing and query capabilities that help investigate threats that may have evaded initial security controls. - Log Data Analysis:
Wazuh’s agents collect logs from the operating system and applications and securely send them to Wazuh’s server for rule-based analysis and mapping. - Detection of vulnerabilities:
Wazuh’s agents collect program inventory data and send this information to Wazuh’s server. The inventory data collected is correlated with continuously updated CVE databases to identify known vulnerable software. - Incident Response:
Wazuh has predefined active responses to perform various countermeasures against ongoing threats. - Normative Compliance:
Wazuh offers some of the security controls required for compliance with industry standards and regulations, such as GDPR, NIST, TSC and HIPAA, also achieved through SCA and FIM functions. - The IT Hygiene:
Wazuh builds an updated system inventory of all monitored end devices. This inventory helps organizations to optimize the visibility of assets and maintain good IT hygiene. - Container Security:
Wazuh provides security visibility to Docker hosts and containers, monitoring their behavior and detecting threats, vulnerabilities and anomalies. - Protection of Work and Integration of third parties:
Wazuh integrates with cloud platforms, collecting and aggregating security data. Alert on security risks and vulnerabilities discovered to ensure safety and compliance with regulatory standards.
Wazuh monitors and protects the work crews in the workplace as well as in the local environment. It can integrate with cloud platforms such as AWS, Microsoft Azure, GCP, Microsoft 365 and GitHub to monitor services, virtual machines and the activities that occur on these platforms.
