Nowadays, internet security is more important than ever. With the growing number of data breaches and cyberattacks, it is crucial to know if our credentials have been compromised. Have I Been Pwned? (HIBP) is a free and accessible tool that allows us to check if our email address or password has been exposed in any data breach.
What is Have I Been Pwned?
Have I Been Pwned? is a platform created by Troy Hunt, a cybersecurity expert, on December 4, 2013. It collects leaked databases and allows users to check if their data has been compromised. When a company suffers a breach, user credentials often end up exposed on the “Dark Web” or on hacker forums. This tool becomes a practical solution for anyone who wants to monitor their information and detect potential vulnerabilities. It provides details about the breach, such as:
- Where, when, and how the breach occurred.
- Compromised data: email addresses, passwords, password hints, or usernames.
How it works?
The use of Have I Been Pwned? is very simple.
- Go to the website https://haveibeenpwned.com/.
- Enter your email address in the search field.
- Prem el botó “pwned?” i espera els resultats.
- If your email address has been exposed in a breach, the website will show you which databases it has appeared in.
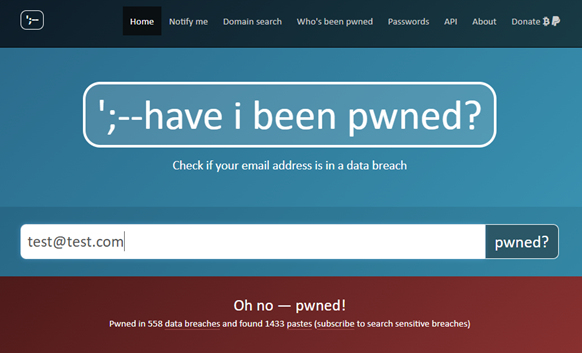
The following image is an example of using the tool, where it can be seen that the entered address has indeed been compromised.
There is also a section to check if a password has been leaked, without revealing it, thanks to a partial hash system. This is useful to avoid reusing compromised passwords and improve account security. This feature can be used from the website or through the API. To maintain password anonymity, NO full password is sent or sent in plain text directly to the API. First, the password to be checked is hashed, and only the first 5 characters are taken. These are sent to the API, which responds with possible suffixes for that password and a count of how many times each has been leaked. What you need to do is search for the rest of the password hash in the list returned by the API (the first 5 characters must be removed).
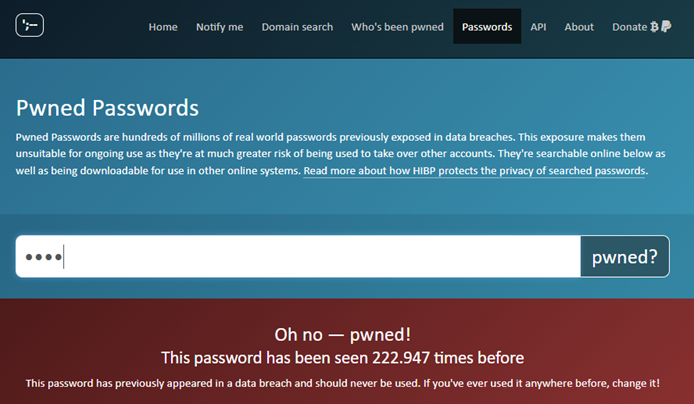
The use of Have I Been Pwned? to check passwords from the website is very simple:
- Go to the website https://haveibeenpwned.com/Passwords.
- Enter your password in the search field (even if you put the password, it is not sent, but a part of the hash is sent).
- Prem el botó “pwned?” i espera els resultats.
- If your password has been exposed in a breach, the website will show you which databases it has appeared in.
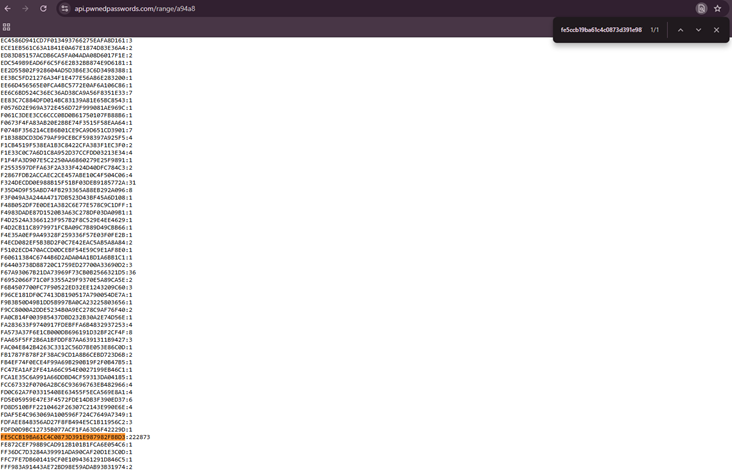
Using Have I Been Pwned? to check passwords via the API is done differently. The following image shows an example of how to use the API. The password that was checked is ‘test’. The first 5 characters of the hash (‘a94a8’) were entered, and it returned a list with all possible continuations. If the rest of the hash for the password ‘test’ (‘fe5ccb19ba61c4c0873d391e987982fbbd3’) is used, it is possible to see if the password has been compromised.
What to do if your information has been breached?
It is possible that when using Have I Been Pwned, you may find that a password has been leaked. It could be an old account, a forum you used to visit but no longer do, a social network you barely log into, or on the other hand, something you do use daily. Whatever the case may be, you should take action as soon as possible to avoid issues that could compromise your security and privacy.
The first thing you should do is, of course, change your password. Ideally, it should be a completely random, strong, and unique password. It should be composed of letters (both uppercase and lowercase), numbers, and also symbols to provide more protection.
In addition to using Have I Been Pwned?, there are other actions you can take to protect yourself. Adopting good digital security practices is essential to avoid risks. These steps are a good guide to improve your internet security:
- Enable two-factor authentication (2FA) to add an extra layer of security.
- Avoid reusing passwords across different accounts.
- Use a password manager to generate and store secure access keys.
- Subscribe to HIBP notifications to receive alerts if your data appears in future breaches.
In addition to changing passwords and activating two-step authentication, it is equally important to adopt a proactive mindset on cybersecurity. Therefore, it is advisable to review the devices from which you access your accounts to detect possible unauthorized access. Avoid accessing unprotected public Wi-Fi networks when managing critical information and make sure to log out of shared devices.
It is also advisable to periodically review online accounts and services, eliminating those you no longer use, and make sure that all applications and operating systems are updated with the latest security patches. Finally, continually educating ourselves about new digital threats and applying adequate protection measures can make the difference between keeping our information safe or becoming victims of cybercriminals.